The Azure Shared Responsibility Model for Cyber Security is a security model that defines the responsibilities of both organizations and users of Azure services. The SRM creates a framework for organizations to create policies that govern how they use Azure while providing guidelines for user actions such as logging in, downloading apps, or accessing storage.
It allows you to identify the responsibilities associated with your Azure resources and then design a solution to help you manage those risks. If you can touch it or it belongs to you, you are liable for it, according to the general principle of shared responsibility. Accordingly, a cloud provider is often in charge of protecting the elements of the cloud that it directly manages, such as the hardware, networks, services, and infrastructure that power cloud resources.
In addition, users are often in charge of protecting everything they build in the cloud, such as the configuration of a cloud workload, specific services, and the infrastructure necessary to construct the desired cloud environment.
Microsoft Azure Shared Responsibility Model for Cyber Security
Microsoft Azure is a cloud platform that allows you to host your applications, data, and platforms in the cloud. Azure has prioritized platform security to safeguard customers’ sensitive data and applications by taking ownership of the security of its infrastructure. In addition, Azure tracks down fraud and abuse and alerts users when an event occurs.
However, it is the customer’s responsibility to make sure their Azure environment is set securely, that data is not shared improperly, and that compliance and governance standards are being followed to detect when an identity (people or non-people) is misusing Azure.
The Shared Responsibility Model in Microsoft Azure works like this:
- Customers are responsible for securing their environments using best practices like:
- They are configuring their virtual machines with firewall rules that allow only approved traffic into their applications.
- Ensuring their directories are protected from unauthorized access by configuring directory services correctly.
- They are enforcing proper account lockout policies on devices such as laptops and mobile devices used by employees in the workplace.
- Monitoring network traffic between on-premises systems and cloud ones.
How Microsoft Ensures Security in the Azure Shared Responsibility Model
The underlying infrastructure’s processing, storage, networking, and database services are safeguarded against incursions by the Azure Shared Responsibility Model.
Azure is also in charge of maintaining the safety of the technology, software, and real estate used to house Azure services. The security setup of Azure’s managed services, including Azure Kubernetes Service, Cosmos DB, SQL, Data Lake Storage, Blob Backup, and others, is handled by the Azure cloud security framework.
The Azure cloud security framework includes four main components:
- Security Services: The Security Services component is responsible for securing your data center infrastructure at rest and in motion. It protects against cyberattacks on physical devices such as servers and workstations by implementing advanced methods like threat detection and response systems that proactively identify threats before they can damage your data or cause loss of confidentiality or integrity.
- Azure App Security: The Azure App Security service helps you keep your apps secure by detecting malicious activity in any apps or code running on your networked devices. It protects from attacks such as Man-In-The-Middle (MITM) and application compromise.
- Azure Key Vault: The Azure Key Vault service helps you securely store keys used to sign certificates used for encrypting.
The Basics of Shared Responsibility In Cloud Computing Contracts
For companies of all sizes, cloud computing has emerged as a popular and straightforward alternative. However, although it is an established technology, the idea of shared responsibility is nevertheless intimidating and sometimes perplexing, primarily because cloud computing has only just gained widespread adoption. Moreover, there are trade-offs to consider, as with other technology.
The benefits are easy to see, such as the following:
- The provider is primarily responsible for the infrastructure’s security in terms of shared responsibility. Users’ worries are reduced, and you can quickly and easily complete jobs with shared responsibility.
- Infrastructure security is a significant focus for cloud providers, who are often highly proficient at it. This can be a considerable advantage for small-to-midsize businesses that need to gain in-house security knowledge.
- Users must trust that cloud providers are delivering on their security responsibilities. This can be difficult for large businesses with sensitive data — and impossible for some types of businesses.
- Users must be thoroughly aware of the provider’s tools, resources, and configuration options to handle half of the shared responsibility and ensure that workloads and data running inside the cloud’s infrastructure are adequately protected, such as employing encryption.
- Users must be aware of any infrastructure or service changes providers make, such as API upgrades, to maintain the security of setups and settings.
Why the Azure Shared Responsibility Model is Important to Your Business
In today’s digital world, security is a significant concern for large and small organizations. Still, it can be especially challenging to strike the proper balance between security requirements and running your business smoothly.
The Azure Shared Responsibility Model is a helpful tool that helps you understand how much responsibility you have in managing your infrastructure. Customers of the Azure Shared Responsibility Model are in charge of the security of “anything in their cloud, or, to put it another way, everything they instantiate, construct, and utilize.”
It is the customer’s responsibility to ensure that multi-factor authentication is enabled for users, especially those with the most granular IAM permissions in Azure, even though the Azure Shared Responsibility Model has implemented many levels of protection to prevent unwanted access to Azure.
It is important to note that the Azure cloud security framework services’ default security settings are frequently the least safe. Therefore, enterprises should prioritize improving these default Azure security settings as the first step in carrying out their share of the Azure security obligation. They should next assess the resources and services they are utilizing to ascertain the desired security levels.
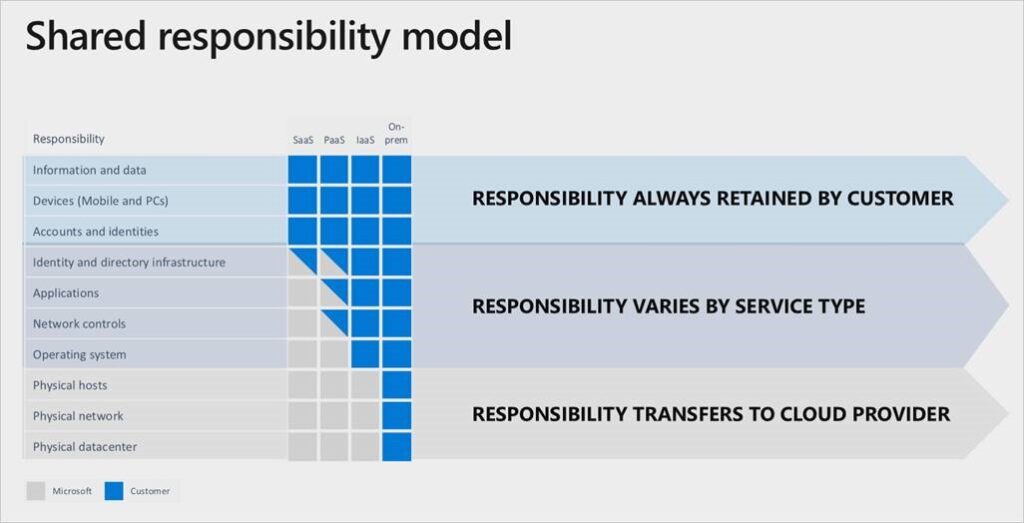
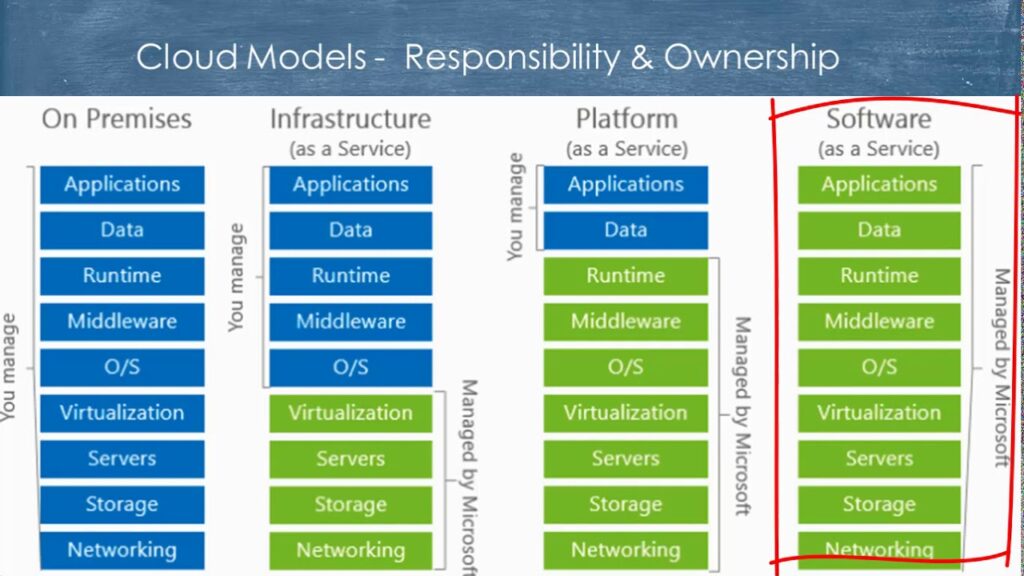
Visualizing Microsoft Azure Cloud Service Deployment Models
Ensuring that your data is accessible, secure, and safe is essential before migrating your application and data to the cloud.
The client owns the whole stack in an on-premises data center. Some of your duties shift to Microsoft Azure as you go to the cloud. The regions of responsibility between the client and Microsoft according to the kind of stack deployment are shown in the following diagram.
You are the owner of your data and identities for all cloud deployment. You are in charge of maintaining the security of your data and identities, as well as the on-premises resources and managed cloud components.
No of the deployment method, you, the Azure client, will always be responsible for the following tasks:
- Data—The data is your responsibility, and you must be able to access and maintain it.
- Endpoints—The endpoint is where you will host your code, a process that can involve many steps. It would help if you had an endpoint up and running at all times.
- Account—You must have an account with Microsoft Azure. You should use this account for all Azure-related activities, including billing, provisioning resources, managing licenses and subscriptions, and reporting on usage.
- Access management—Access management lets you limit who gets access to your resources differently depending on their roles (such as administrators vs. developers).
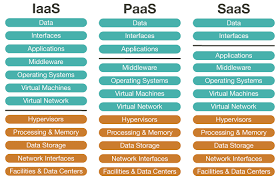
SaaS vs. PaaS vs. IaaS: Similar But Different
The idea of shared responsibility applies to each of these cloud delivery methods. However, ownership of security duties and functions varies depending on the delivery model used. There are three primary models for cloud services:
- Software as a service (SaaS)
SaaS refers to a software delivery paradigm where a vendor centrally hosts a subscriber-accessible application in the cloud. In this approach, the provider is in charge of managing and maintaining the application as well as its security.
With SaaS, the vendor maintains a server that hosts all applications for the subscriber. The vendor provides access to users through a browser-based user interface and allows them to interact with the application without downloading or installing it on their computer. Users only pay for what they use, so there’s no need to buy additional licenses or hardware that they might not need.
- Infrastructure as a service (IaaS)
IaaS is a method of delivering infrastructure in which a vendor offers a variety of computing resources, including virtualized servers, storage, and network hardware, via the internet. According to this approach, a company is in charge of keeping everything they control or install just on cloud infrastructure secure, including the operating system, apps, middleware, containers, workloads, data, and code.
The company only pays for what they use and is free to increase or decrease as required incurring additional costs or penalties. A cloud host offers support, maintenance, and tools for controlling its infrastructure.
- Platform as a service (PaaS)
PaaS is an acronym for platform as a service, and you can use it to create, manage, and execute applications. The vendor offers the hardware and software in the cloud platform model application developers typically employ. The service provider is also in charge of maintaining the platform’s and its infrastructure’s security.
PaaS is often used to build on-demand software applications or services in which the application developer does not need to worry about managing their servers or infrastructure. Instead, the application developer only needs to worry about coding their application and interacting with it through an API interface.
Microsoft Azure Security Best Practices Offered By EPC Group
In summary, the Azure Shared Responsibility Model is a way to ensure that organizations devise a system that can help them implement security effectively. It helps them meet the standards for safeguarding their data, protect the financial and reputational risks associated with data breaches, and ensure that they provide defenses that are commensurate with their responsibilities.
To manage your security, you need a scalable and cloud-native SIEM. MS Azure Sentinel can help with that. It provides a solitary answer for alert detection, reactive searching, risk monitoring, and action to attacks. It will help you reduce the stress of extended resolution time frames, increasing volumes of alerts, and growing cyber-attacks. And EPC’s Azure Sentinel specialists can help you get the best out of it for your organization.










