You may leverage existing on-premises Active Directory indicators to identify, detect, and look into emerging attacks, compromised identities, and hostile insider behaviors targeted at your company using Azure Advanced Threat Protection (ATP).
Azure ATP helps analysts and security experts who struggle to identify sophisticated threats in hybrid settings by utilizing learning-based analytics and putting incident information on a specific timeline for quick triage.
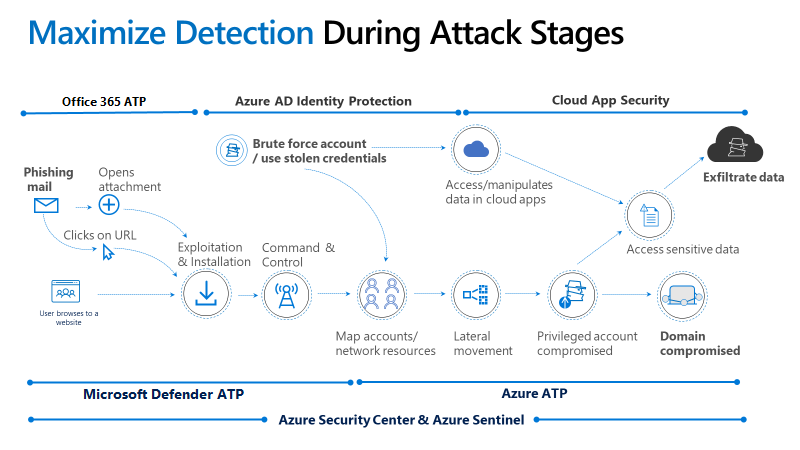
Suppose you’re an analyst or security professional in an environment where users access corporate resources outside the corporate network. In that case, you may have a hard time detecting malicious activities:
- You may use analytics based on learning to track user behavior, entity behavior, and activity.
- Safeguard the user identities and login information kept in Active Directory.
- Determine and look at advanced attacks and nefarious user activity throughout the kill chain.
Azure Advanced Threat Protection Features Explained
- Azure Advanced Threat Protection portal
The Azure ATP portal is a tool that allows you to create and manage your Azure ATP instance, display the data received from Azure ATP sensors, and enable you to monitor, manage, and investigate threats in your network environment.
- Azure Advanced Threat Protection sensor
The Azure ATP sensor is deployed on your domain controllers as a direct-attach security gadget. Without a dedicated server or the setup of port mirroring, the sensor immediately observes domain controller traffic. The sensor also offers many other features that aren’t available with port mirroring, such as real-time threat detection and data loss prevention (DLP) integration.
- Azure Advanced Threat Protection cloud service
Azure ATP cloud service is a scalable and secure cloud platform that runs on Azure infrastructure. It provides advanced threat protection for your digital assets and delivers scalable services that you can use to meet the needs of any business. In addition, the service is connected to Microsoft’s intelligent security graph, which helps you make informed decisions about ways to protect your data and comply with legal regulations.
How To Stay Secure With Azure ATP
Azure Advanced Threat Protection security alerts are designed to help you understand precisely what is happening on your network. They describe the suspicious actions on your network, the people and computers responsible for the risks, and how they were discovered using simple language and images.
Alerts are categorized by threat phase, color-coded to make them easier to filter visually, and rated for severity. Each alert is intended to provide you rapid access to precise information about what is occurring on your network. In addition, alert evidence listings include direct connections to the concerned machines and users so that you may conduct quick and efficient investigations.
How Azure Advanced Threat Protection powers the new Security Center
Azure Advanced Threat Protection (ATP) powers the new Security Center, providing organizations with the intelligence they need to help protect their users, assets, and the data they use.
Azure Advanced Threat Protection monitors and analyzes user activities and information across your network, such as permissions and group membership. For each user, it establishes a behavioral baseline. Azure ATP then uses adaptive built-in intelligence to detect abnormalities, providing insights about shady behaviors and occurrences and exposing the advanced threats, compromised users, and insider threats your company is experiencing.
Azure ATP’s proprietary sensors monitor organizational domain controllers, providing a comprehensive view of all user activities from every device. In addition, the new Security Center provides advanced threat detection so that you can stop attacks before they happen.

Azure ATP Reduces Your Attack Surface With Visual Lateral Movement Paths And Clear-Text Password
Azure Advanced Threat Protection helps you reduce your attack surface with visual Lateral Movement Paths and a clear-text password.
Azure ATP provides invaluable insights on identity configurations and suggested security best practices. In addition, through security reports and user profile analytics, Azure ATP significantly reduces your organization’s attack surface, which makes it more challenging to steal user credentials and carry out advanced assaults.
With Azure ATP’s visual Lateral Movement Paths, you can instantly identify the steps an attacker would take to compromise important accounts inside your business. This might assist you in taking preventive actions before the danger arises.
Security reports from Azure Advanced Threat Protection give you more information to strengthen your organization’s security posture and policies and assist you in detecting people and devices that verify using clear-text passwords.
How Azure ATP detects Advanced Threats
Attacks are typically launched against any accessible entity, such as a low-privileged user. This means the attacker can quickly move laterally until they gain access to valuable assets—such as statements, domain admins, and sensitive information. Azure Advanced Threat Protection recognizes sophisticated threats at the point of origin along the complete cyber-attack kill chain.
- Spot Rogue Users And Attacks
Rogue users and attackers are searching for information about user names, users’ group membership, IP addresses assigned to devices, resources, and more. These attackers are using various methods to identify information about user names, user groups, Systems, services, and other things given IP addresses.
- Compromising Credentials Detection
There are several ways that credentials can be compromised. The first is brute-force attacks. When a user account has been compromised, the attacker will attempt to log into their account as many times as possible until they succeed.
You can do this by using a program or script that attempts to guess passwords using a list of known or shared passwords. The second way is by failing authentication attempts. This can occur when an attacker uses an automated process to try and authenticate against a web application and receives a response that doesn’t match what they expected.
- Maturing From Theory To Practice
Previously, the only method to get a user’s account was to get past the user’s password. However, several methods exist for accessing an account without their knowledge or consent. These include:
- Pass the Ticket: This is where an attacker obtains a valid ticket from a legitimate user (the target). The attacker uses this ticket to log into the target’s account, change their password, or install malware on their computer.
- Pass the Hash: In this attack, an attacker obtains the hash value of a password and then uses it to guess other users’ passwords, thereby gaining unauthorized access to their accounts.
- Overpassing the Hash: This is where an attacker obtains both a valid ticket and its corresponding hash value so that they can use one password to log into multiple accounts with different values.
- Attacker Behavior In Domain Dominance
Attackers use domain controllers to execute remote code, allowing them to take over a network and gain control of other computers. The more powerful a domain controller is, the more likely it will be able to run malicious code remotely.
In addition, attackers can also use domain controllers to create replica domain controllers that can spread across the network and allow access to any computer that trusts these DCs. These replica DCs are created by injecting malicious code into legitimate ones or using Golden Ticket activities such as DCShadow and Dridex.

Get Azure ATP and Windows Defender ATP for Advanced Threat Prevention
Microsoft Azure Advanced Threat Protection (Azure ATP) provides advanced threat protection for Microsoft Azure resources, including virtual machines, web applications, and cloud services. In addition, it provides a real-time attack timeline that shows all threats that have been detected. You can use the information in this timeline to quickly investigate threats and gain insights across your organization for users, devices, network resources, and more.
Azure ATP is meant to offer just the most pertinent warning signals in a straightforward organizational attack chronology, reducing general alert noise. By utilizing the expertise of intelligent analytics, the attack timeline view makes it simple for you to stay focused on what counts. Use Azure ATP to quickly investigate threats and gain insights across your organization for users, devices, network resources, and more.
By adding extra detection and defense from advanced persistent threats on the computer system, an integrated solution with Windows Defender ATP adds a layer of enhanced security.
EPC Group Is Ready To Help You Get Started with Azure Sentinel Consulting Services
Azure Advanced Threat Protection is an affordable way to enhance an organization’s security posture analysis. It can help identify attacks, compromised identities, and hostile insider behavior. Deploying it requires the creation of a Security Monitoring workspace, which will enable you to define what you want to monitor by specifying various logging sources.
After that, create a Security Analysis workspace to analyze the data generated. The Security Analysis workspace is where you use analytics, investigation, and attribution services to discover threats and advanced capabilities like graph analysis and actionable insights.
Microsoft’s latest product in the realm of cloud-native cybersecurity. It empowers you to maximize ROI with the right mix of security, automation, and analytics. The Azure Sentinel experts at EPC Group can assist you in making the most of it for your business.










