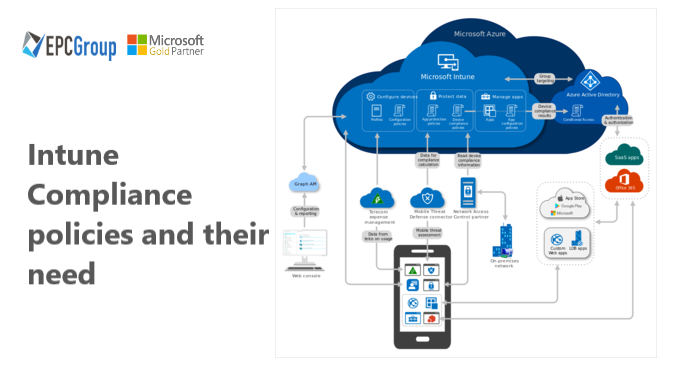
An Intune compliance policy is crucial for organizations to ensure the security and management of their mobile devices and applications, protecting sensitive data from potential threats.
Apart from Compliance policies, organizations can also benefit from Configuration and Security policies to maintain a secure and streamlined IT environment.
- Configuration policies focus on setting up devices and applications according to specific organizational standards, such as enforcing Wi-Fi settings or email configurations.
- Security policies emphasize safeguarding devices and data by implementing encryption, password requirements, and data access restrictions.
While Compliance policies ensure devices adhere to organizational security requirements, Configuration and Security policies concentrate on customizing device settings and fortifying data protection.
Overview of Device Compliance Dashboard in Microsoft Intune for monitoring results
The Device Compliance dashboard in Microsoft Intune offers a centralized monitoring platform, providing essential insights into the compliance status of devices within an organization, allowing admins to identify and resolve any security-related issues quickly.
With trend analysis, policy breakdown, and drill-down capabilities, admins can efficiently track compliance status, identify potential issues, and take appropriate actions to maintain a secure and compliant IT environment.
- Dashboard Overview: Provides a high-level view of device compliance status within the organization.
- Compliance Trends: Displays trends over time, highlighting improvements or issues that need attention.
- Non-compliant Devices: Shows a list of devices that do not meet the compliance policy requirements, allowing admins to take necessary actions.
- Top Compliance Policies: Highlights the most impactful compliance policies, enabling a focus on critical aspects of device security.
- Policy Compliance Status: Breaks down the compliance status of individual policies, showing compliant, non-compliant, and not applicable devices.
- Filter and Export Options: Admins can filter results based on specific parameters and export data for further analysis or reporting.
- Drill-down Capabilities: The ability to click on specific metrics to view more detailed information or perform actions such as sending compliance notifications.
How to Manage Microsoft Intune Compliance Settings
Managing Microsoft Intune Compliance Settings is essential for organizations to ensure their devices meet specific security and policy requirements. By creating and configuring compliance policies, administrators can maintain a secure IT environment, monitor device compliance, and quickly address any issues.
The following list of procedures gives a general idea of how to manage Intune Compliance Settings efficiently:
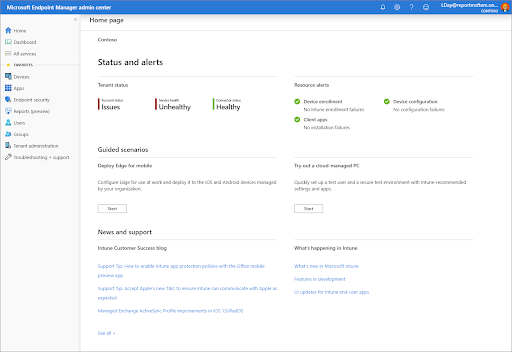
Step 1: Sign in to Microsoft Endpoint Manager admin center
- Go to https://endpoint.microsoft.com/ and sign in with your admin credentials.
Step 2: Navigate to the “Devices” section
- Click on “Devices” in the left-hand menu.
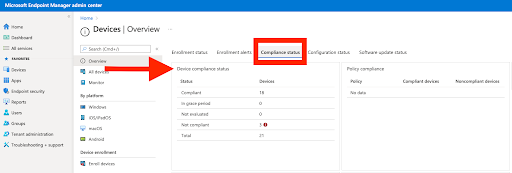
Step 3: Access “Compliance policies”
- In the “Devices” section, click on “Compliance policies” under the “Policy” category.
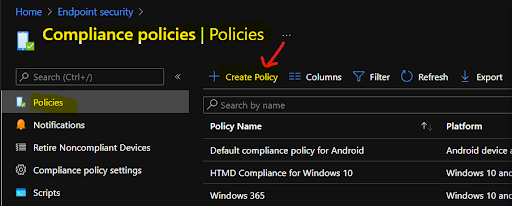
Step 4: Create a new compliance policy
- Click on the “Create Policy” button.
- Choose the platform (e.g., Windows, iOS/iPadOS, Android, etc.) for which you want to create the compliance policy.
- Click “Create” to proceed.
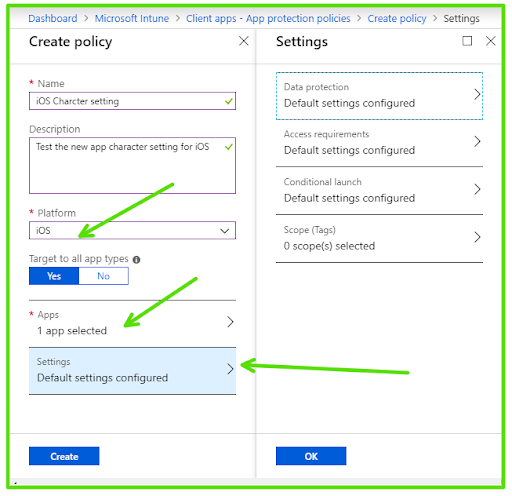
Step 5: Configure the policy settings
- Enter a name and description for your new compliance policy.
- Configure the required settings based on your organization’s security requirements, such as password settings, encryption, device health, and more.
Step 6: Save and assign the policy
- Click “Next” to review the settings and proceed to the “Assignments” section.
- Click “Select groups to include” and choose the user groups to which this policy should apply.
- Optionally, you can also choose groups to exclude if needed.
- Click “Next” to review the settings one more time, and then click “Create” to save and assign the policy.
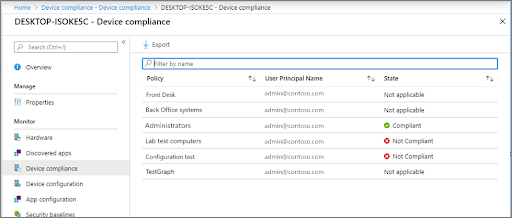
Step 7: Monitor policy status and compliance
- Go back to the “Compliance policies” page, and you will see your newly created policy in the list.
- Click on the policy to view its details and monitor the policy status and device compliance.
Understanding Conditional Access policies and their uses in device management
Conditional Access policies are a powerful tool in Microsoft Intune that helps organizations secure their resources by enforcing specific conditions for access.
These policies allow administrators to control how and under what circumstances users can access organizational resources, such as applications, data, and services.
Conditional Access policies can be based on various factors, including:
User Identity
To ensure that only authorized people may access particular resources, policies can be applied to particular users or user groups.
Device Compliance
Access can be granted only to devices that meet compliance requirements, such as having a specific operating system version, encryption enabled, or up-to-date security patches.
Location
Access can be restricted based on the user’s geographical location, ensuring that resources are only accessible from approved locations, such as a corporate office or a secure network.
Sign-in Risk
Policies can evaluate the risk level of a sign-in attempt based on factors like unfamiliar locations, impossible travel scenarios, or unusual behavior patterns. Access can be denied or limited for high-risk sign-ins.
App Protection
Conditional Access policies can be used to require app protection policies for specific applications, ensuring that data accessed through these apps is protected even when accessed from personal devices.
Uses of Conditional Access policies in device management include:
- Enforcing multi-factor authentication (MFA) for sensitive resources, adding an extra layer of security.
- Requiring users to access resources from managed devices, ensuring that unmanaged or personal devices cannot access sensitive data.
- Blocking access to resources from specific countries or regions, reducing the risk of unauthorized access or data breaches.
- Limiting access based on time of day, ensuring that resources are only available during approved working hours.
- Requiring devices to be compliant with specific security settings, such as encryption and password requirements, before granting access to resources.
Microsoft Intune Compliance Policies With Actions For Non-Compliance
Microsoft Intune Compliance Policies play a vital role in ensuring that devices within an organization meet specific security and configuration requirements.
One of the key features of these policies is the ability to define actions that will be taken when a device is found to be non-compliant. This helps administrators maintain a secure IT environment by automatically addressing potential security risks.
Some common actions for non-compliance include:
Mark the device as non-compliant
This action can be taken in response to a non-compliant device, changing the device’s compliance status to non-compliant within the Microsoft Intune system. The primary purpose of marking a device as non-compliant is to signal that it does not meet the organization’s predefined security and configuration requirements.
Send an email to the device’s user
This action sends a notification email to the user, informing them that their device is non-compliant and providing guidance on how to resolve the issue. To ensure the security and stability of our network, it is important that all devices connected to it meet the minimum security and compliance standards. Your device does not meet these standards, and as a result, it may be vulnerable to security threats and negatively impact the performance of the network.
Send push notification to the device
This action utilizes the power of push notifications to inform users in real-time about non-compliance issues detected on their devices. By immediately delivering a push notification to the device, users receive immediate alerts about any security or configuration problems, prompting them to address the concerns quickly. This method of communication is highly effective, as it ensures that the user is aware of the non-compliant status and can take appropriate corrective actions to resolve the issue.
Remotely lock the device
In situations where non-compliance is particularly severe or poses a significant security risk, administrators have the option to remotely lock the affected device, ensuring the protection of sensitive data and minimizing the potential for unauthorized access. When a device is remotely locked, users are unable to access any data or applications on the device until the non-compliance issue has been resolved and the device is deemed compliant with the organization’s policies.
Retire or wipe the device
As a last resort, when other actions fail to bring the device back into compliance or when the risk of data leakage is deemed too high, administrators can opt to retire or completely wipe the device. This process removes all organizational data, applications, and configurations, ensuring that sensitive information is not compromised. In the case of a complete device wipe, the device is returned to its factory settings, effectively erasing all data and settings, both personal and organizational.
To configure actions for non-compliance in a Microsoft Intune Compliance Policy, follow these steps:
- Navigate to the Microsoft Endpoint Manager admin center and access the “Compliance policies” section under the “Devices” menu.
- Select an existing policy or create a new one.
- In the policy settings, locate the “Actions for non-compliance” section.
- Click “Add” to configure a new action, choose the desired action type, and specify the time delay before the action is taken.
- Save and assign the policy as needed.
Understanding Limitations and Challenges of Device Management Through Intune
Although Microsoft Intune offers powerful device management capabilities, organizations may face certain limitations and challenges when implementing and managing their devices through Intune. Understanding these limitations and challenges is crucial to successfully navigate the complexities of Intune and ensure a secure, efficient, and productive IT environment.
| Limitations and Challenges | Description |
| Application Management | Intune’s app management capabilities may not be as extensive as some third-party solutions, limiting app deployment options. |
| Complex Setup | Intune’s initial configuration may be challenging and difficult, requiring a thorough knowledge of the platform and all of its capabilities. |
| Device Platform Support | While Intune supports major platforms like Windows, iOS, and Android, support for some niche platforms may be limited. |
| Network Bandwidth Constraints | Deploying large applications or updates across multiple devices can lead to network congestion and reduced performance. |
| Integration with Third-Party Solutions | Intune may not seamlessly integrate with all third-party applications, requiring additional configuration or workarounds. |
| Limited Customization | Some organizations may require more customization options than what Intune provides out of the box. |
| Cost | Intune licensing costs can be significant, especially for large organizations with numerous devices and users. |
| Frequent Updates and Feature Changes | As Microsoft continually updates and improves Intune, organizations must adapt to changes and ensure their knowledge is current. |
| User Resistance | Users may resist new device management policies and restrictions, leading to reduced productivity and potential pushback. |
Maximize Security and Productivity with EPC Group’s Intune Services and Management
Our team of experts provides tailored guidance, consultation, and support to help your organization effectively implement and manage Microsoft Intune. By leveraging our expertise, you can overcome any limitations or challenges associated with Intune, ensuring a secure and efficient IT environment.
We provide comprehensive services including seamless implementation, app and device management, security and compliance assistance, and user training and adoption support. Our experienced consultants work closely with your organization to understand your unique requirements and develop customized Intune strategies that meet your specific needs.
Don’t let the complexities of Intune hold your organization back from achieving its full potential. Partner with our Intune Services and Management team to unlock the true power of Microsoft Intune and create a secure and productive IT environment for your organization.
Contact EPC Group today to discover how they can help your business excel with Intune, and experience the benefits of a well-managed and secure mobile device ecosystem.