The term CMMC is the abbreviation of the phrase Cybersecurity Maturity Model Certification. This is a part of the United States Department of Defense initiative to normalize the preparedness for cybersecurity measures all over the defense industrial base or DIB within the federal government. In this blog post, we will go over all CMMC Certification Levels in detail.
The certification initiative was designed as a program to measure the level of sophistication and receptiveness that the defense contractors possessed. As the contractors at the Defence Industrial Base deal with controlled unclassified information, it is essential to ensure that they meet the much-needed cybersecurity requirements. The complete process of ensuring these requirements are met, is considered as the CMMC.
CMMC Certification Levels details
Organizations that require CMMC Compliance:
At the basic level, the primary focus of the certification is the improvement in the security framework applied for handling the controlled unclassified information or the CUI and federal contract information or FCI. As this information is constantly accessed and utilized by defense contractors, it is essential to ensure their security.
The certification applies to all types of defense contractors including both prime and subcontractors. Although according to the program, from 2026, some level of certification will be a necessity for any contract, contract requests will still be sent at lower levels of certification too, this has led organizations actively look for CMMC Consulting experts.
Various levels of CMMC Levels:
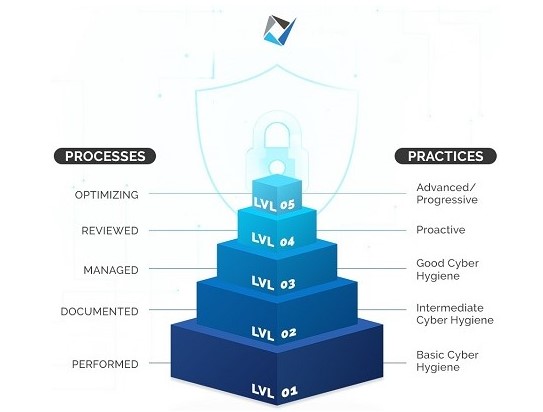
The CMMC certification level is considered as a range of maturity that an organization needs to achieve to work for the Department of Defence (DOD). The level of maturity that will be required depends on the vulnerability of the information that is to be used. These levels of maturity or certification can be categorized according to the increasing order of sensitive information tackled by the organization.
The categorization is done in the following manner:-
- CMMC Level 1
- CMMC Level 2
- CMMC Level 3
- CMMC Level 4
- CMMC Level 5
In addition to these levels, a new maturity level has been introduced recently and has been termed CMMC 2.0.
Also read : CMMC Compliance checklist
CMC Level 1: Meaning
The CMMC Level 1 is the first level in the hierarchy of certifications within the framework. This level can be explained as follows:-
- The processes that form a part of this level are performed by the organizations. In other words, the organizations intending to get certified at this level need to perform certain specific practices.
- The practices need to be performed only in an ad-hoc manner which may or may not include the use of documentation.
- The extent of process maturity is not determined or judged at this level.
- The practices that form a part of this level generally encompass basic cyber hygiene.
- Level 1 is specifically designed for the protection of the Federal Contract Information or the FCI.
- It consists of practices that are corresponding to the general security requirements that are specified in the 48 CFR 52.204-21.
- It is to be well understood that whichever level of certification the defense contractors intend to achieve, they would have to begin at Level 1.
- The basic security requirements demanded by this level are non-negotiable and need to be set right to achieve other levels of maturity.
The CMMC Level 1 can be achieved by smaller companies and comprises a set of common security requirements that are universally accepted. As maturity in the cybersecurity processes is not expected at this level, the organizations applying at this level are not expected to deliver at that height. Thus, this level provides limited security against the exhilaration of data and malpractice.
CMMC Level 2: Explanation
The CMMC Level 2 is more commonly referred to as a bridge to the next level. Generally, defense contracts either have Level 1 certification or directly a certification of Level 3. But, certain situations need to be addressed before the jump to Level 3 can be made. These are dealt with in Level 2. The facts of this CMMC Certification Levels can be enumerated as:-
- This level is an important milestone to be achieved by the defense contractors where the focus is laid on intermediate cyber hygiene.
- The level creates a necessary progression from the previous level to the next.
- Along with the Federal Contracts Information, this level begins to introduce protections related to Controlled Unclassified Information of the CUI.
- In comparison to the previous level, Level 2 places the organizations in a better stand for defending the information against dangerous cybercrimes.
- Along with the additional practices, this level also begins to include the process maturity component of the CMMC model.
- At this level, the attempting organization is expected to perform as well as document all the essential cybersecurity functions.
CMMC Level 3: Description
The third level in the procedural maturity framework builds on the previous level. This implies that the level includes the Federal Acquisition Regulation or FAR practices and about twenty others that support cyber hygiene. The important aspects of this level are:-
- The emphasis of this level is on laying out the importance of planning and keeping up the cybersecurity efforts within an organization.
- The Level 3 clearance is required specifically for companies that create or have access to Controlled Unclassified Information. In the general line of classification, the levels are created in the hierarchy of ‘Basic Hygiene’ to ‘Advanced or Progressive’. Concerning this categorization, Level 3 is considered as ‘Good Cyber Hygiene.
- This level includes all the requirements of the previous levels in addition to some others. These additional requirements are designed to focus on the planning, sourcing, and reviewing of the security policies and procedures implied by the contractor organizations.
- Although this level of certification is higher than the previous ones, the organizations clearing this level may still be unsuccessful in defending the information against advanced security threats.
- As there are significantly more controls in Level 3 than those in Level 1 and 2, the required processes to be executed range to about 130 that are categorized into approximately 7 domains.
CMMC Level 4: Meaning
Level 4 of CMMC signifies a substantially proactive cybersecurity program. This level is one of the important levels of this certification hierarchy. The facts of this level can be described as follows:-
- The organizations that successfully achieve this certification, depict the ability to adapt to the protective measures required during cyber threats.
- The preparedness of the organizations helps them to respond aptly to the changing methods, tactics, and procedures used during advanced persistent threats or APTs.
- At this level, the organizations are required to review and measure their cybersecurity practices and determine their effectiveness.
- Additionally, these defense contractors must depict the intention of taking corrective actions when necessary and inform the higher management frequently.
- This level focuses on the protection of the Controlled Unclassified Information from the Advanced Persistent Threats.
- Along with this, the certification also includes a set of enhanced security measures and best practices. These practices are essential in the sense that these help in improving the responsive capabilities of the organizations.
- The controls within this level include the 130 controls from the previous level and 26 others.
CMMC Level 5: Description
The final CMMC Certification Levels within the certification hierarchy consists of the CMMC Level 5. This level needs the defense organizations to standardize and optimize the implementing processes in an advanced manner across the whole organization. The facts of this level include the following:-
- Building upon the practice approaches included in the previous level, this level focuses on the protection of Controlled Unclassified Information from Advanced Persistent Threats.
- Although the focus of the controls is not any different from the previous level, the additional controls and procedures help in delivering a deep and sophisticated cybersecurity framework within the certified organization.
- This level is also known as the Advanced or Progressive cyber security posture which seeks to reduce the damages caused by the Advanced Persistent Threats.
- In theory, levels 4 and 5 both need more security measures and a vigilant attitude on the part of the defense contractors than the previous levels, Level 5 requires a more advanced framework of proactive scanning and recognition of Advanced Persistent Threats.
- This level additionally also needs the organizations to manage the ongoing procedures and optimize the processes to continuously protect against the evolving threat attempts.
CMMC 2. O: Overview
The CMMC 2.0 is the new addition to the cybersecurity model of the Department of Defence. The new intermediate level streamlines all the requirements of the three levels of cybersecurity including the Foundational, Advanced, and Expert.
The requirements at this level align with the requirements at each of these levels along with the widely accepted NIST standards of cybersecurity. With the implementation of the CMMC Level 2.0, the department intends to bring about certain changes to the CMMC model 1.0. These changes can be classified in the following manner:-
- Description of levels – Model 1.0 consisted of 5 levels in which Levels 2 and 4 were intermediate steps to Levels 1, 3, and 5. In model 2.0, the 3 Progressive levels would be:
- Foundational level (imitates level 1)
- Advanced Level (imitates level 3) and
- Expert Level ( imitates level 5)
- Requirements at the levels – In the 2.0 model, the maturity processes of the 1.0 model are eliminated. Certain unique practices are also done away with.
Choosing the best CMMC Level for a specific organization:
The framework is classified into 5 CMMC Certification Levels. The Department of Defence contractors is not required to comply with the credentials of all the levels. Instead, specific contractors need to be certified in performing processes that adhere to the protection of the information they handle. For instance, a contractor that remains at the bottom of the supply chain needs to be certified in only Level 1 controls.
On the other hand, contractors assigned the construction contracts of military bases need to be clarified at the highest level. To determine the level of CMMC Certification a certain organization is required to have, it is essential to see where the Federal Contracts Information and the Controlled Unclassified Information are stored and how. After the Readiness assessment has been completed, figuring out the required CMMC certification is quite simple.
Creating a CMMC framework:
To build a proper CMMC framework, the defense contractors should begin with meeting the 110 standards provided by the NIST 800-171. The preparation to meet these standards should not be delayed as the completion of the procedure can take up to a year and a half.

EPC Group: The CMMC compliance partner
The EPC Group is a leading Managed Security Services Provider for CMMC Certification Levels in the U.S. The experience this organization has in implementing cybersecurity measures, accessing the maturity standards, and applying the government guidelines, makes them incomparable. This makes the company a go-to third-party assessor that initiates the CMMC certification procedure. Additionally, the EPC Group has the required technical expertise in the field to conduct readiness assessments and perform a gap analysis.
Along with helping through the compliance procedure, the Group will help the organization in maintaining a CMMC compliant environment by monitoring, detecting, and reporting cybersecurity crimes in a constantly evolving technological environment. This gives the client organizations to address their vulnerabilities and update the currently operating security plan. Also, the EPC Group helps its clients in scheduling the CMMC audits through a certified 3PAO.










